Adding HTTPS Security to the LEADTOOLS Media Server
This topic outlines how to create a test certificate and add a certificate to the LEADTOOLS Media Server demo. The toolkit can support certificates in any store; however, the demo applications enumerate the stores "MY" ( displayed as "Personal" in the Windows consoles) and "Web Hosting".
Secure streaming (HTTP over SSL) is disabled by default. To enable it, two things need to be done:
- Select the SSL port: either 443 (which is default) or an unused port (typically above 1024).
-
Select a security certificate. Two choices are available here:
-
Use a development certificate, which will be valid for initial testing, but not for a proper web site. A development certificates can be obtained in two ways:
- Use a certificate generated by the Media Server demos (easiest)
- Manually create a test certificate using a tool like makecert.
- Obtain a proper certificate from one of the recognized certificate authorities (like IdenTrust, DigiCert, Comodo, GoDaddy, etc).
-
Use a development certificate, which will be valid for initial testing, but not for a proper web site. A development certificates can be obtained in two ways:
If a development certificate is used it will typically work for testing on the local computer; but in order to access the HTTPS stream from another computer, the certificate used on the server needس to be imported on the client computer. The procedure differs from browser to browser, but will typically involve importing the server's certificate into the Trusted Certificate Authorities list.
Below are the steps for selecting a self-generated certificate.
Adding a Certificate to the LTMS Server Demo
-
Open the LTMS server demo. The screenshots below are from the C++ demo, but similar options are available in the C# demo.
-
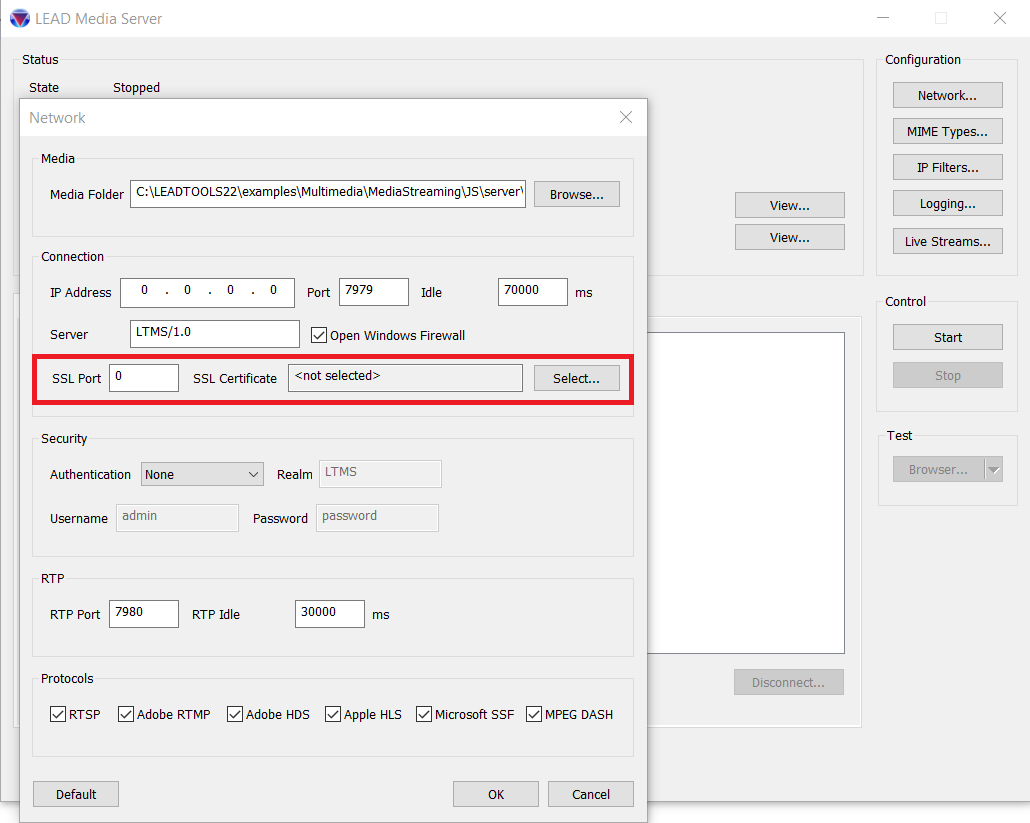
Click the "Network" button.
-
Enter a port number for the SSL port to use (433 is the default, but that is in use sometimes by IIS, so it is better to use 1443).
-
Click the "Select" button next to the SSL Certificate field.
-
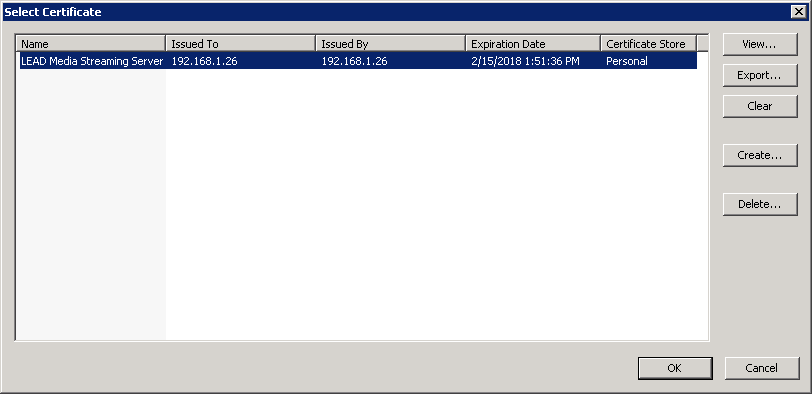
Use the Select Certificate dialog to select certificates from the My/Personal Store or the Web Hosting Store. Create a test certificate by clicking the "Create..." button or delete a certificate by highlighting the certificate and clicking the "Delete..." button.
-
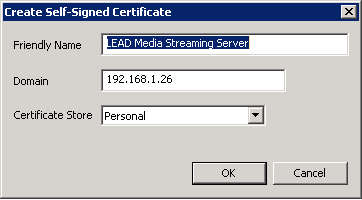
Create a certificate using a friendly name and the IP address of the server or its hostname.
-
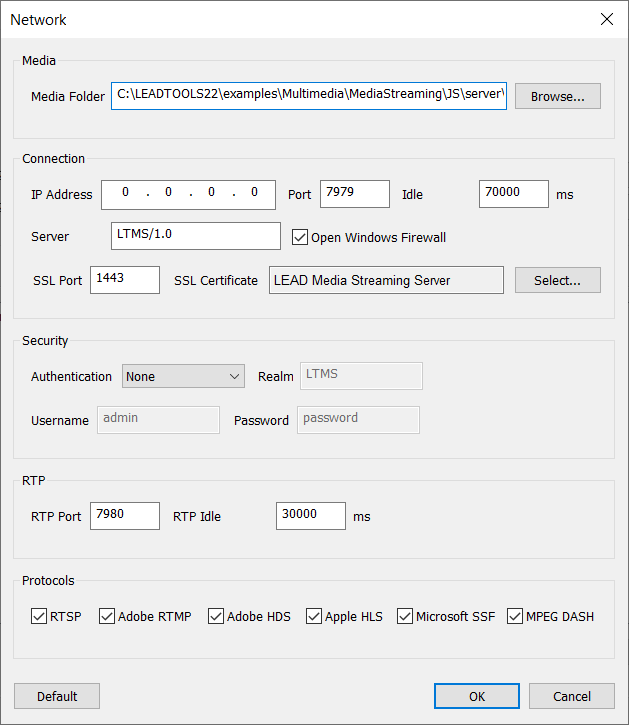
Select a certificate and click OK.
-
The server is now configured for SSL. Start the server.
Accessing a Secure Page
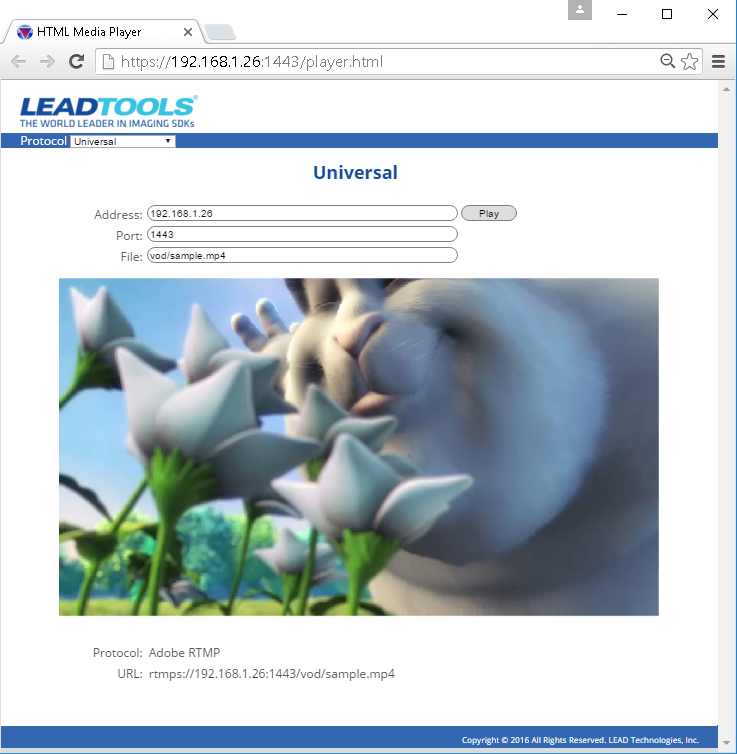
To access the demo html pages. Enter https://address:ssl_port/player.html in a web browser.
If the web page is accessed from a computer other than the server using a development security certificate, the development certificate used by the server will need to be imported into the browser's list of trusted certificates. See the Importing the Development Certificate note below for more details.
Manually Creating a Test Certificate
If an SSL certificate is not available and you wish to manually create one, the following steps illustrate how a certificate can be created using Microsoft's makecert.exe utility.
- Start a Visual Studio command prompt as administrator (elevated).
NOTE: Make sure the version of makecert.exe used is v4.5 or newer (included with VS2012 and up), which supports the sha256 algorithm.
Type "makecert -!" and make sure the algorithms listed for the -a option includes both sha256 and sha1. The makecert.exe program can be copied from another computer, but it must support sha256.
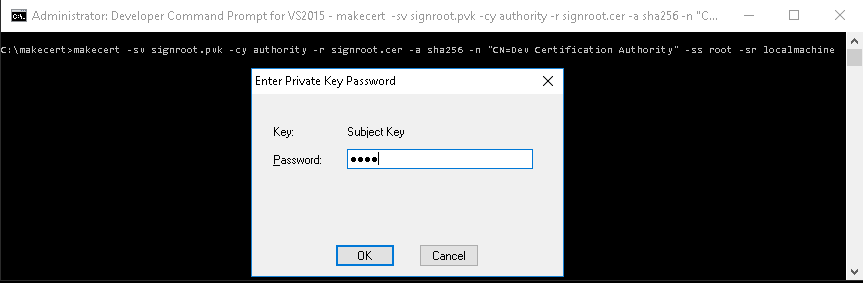
- Use makecert.exe to create a self-signed root certificate that can be used as a Certificate Authority. The certificate is automatically stored in the Trusted Root Certificates Authority (root) store:
makecert -sv signroot.pvk -cy authority -r signroot.cer -a sha256 -n "CN=Dev Certification Authority" -ss root -sr localmachine
signroot.pvk is the name of the generated private key file and is used to sign additional certificates. This may be changed to suit the user's needs. It is needed in the next step as well.
signroot.cer is the name of the generated root certificate, and is used to sign additional certificates. It can also be imported into browsers to avoid a security warning when the server page is access. This may be changed to suit the user's needs. It will be needed in the next step also.
Dev Certification Authority is the internal certificate name. This is the name that will display in any certificate viewer application. This may be changed to suit the user's needs.
-
A prompt will be displayed to provide a password for the private key:
-
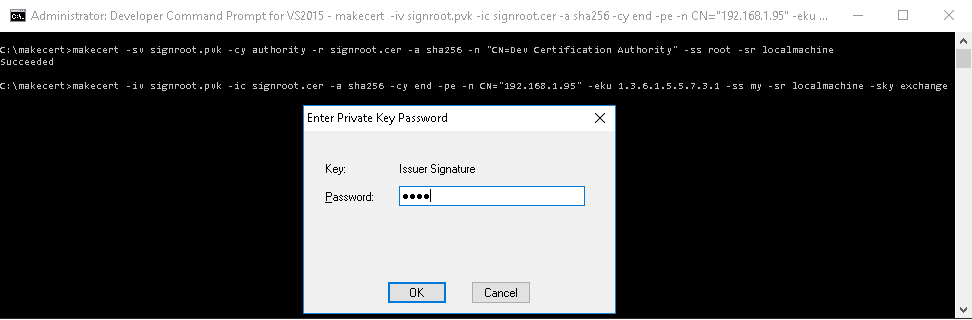
Use makecert.exe to create a host certificate for HTTPS communication. The host name in the certificate must match the host used when calling the self-hosted service. In the example below, modify the loopback address of 127.0.0.1 with the IP address (or with the hostname) of the server. The certificate is automatically stored in the Personal (my) store:
makecert -iv signroot.pvk -ic signroot.cer -a sha256 -cy end -pe -n CN="127.0.0.1" -eku 1.3.6.1.5.5.7.3.1 -ss my -sr localmachine -sky exchange
makecert -iv signroot.pvk -ic signroot.cer -a sha256 -cy end -pe -n CN="LTMS Media Server" -eku 1.3.6.1.5.5.7.3.1 -ss my -sr localmachine -sky exchange
Importing the Development Certificate on Client Computers
Development certificates will be recognized by browsers only when they run on the media server. To play a https stream on another computer, the development certificate used by the server will need to be imported as a Trusted Certificate Authority. Different browsers look to different places for certificates:
- Chrome, IE, Edge, and Opera on Windows all appear to use the system certificate stores.
- Firefox has its own store. The root certificate will need to be imported in the Certificate Manager by clicking View Certificates... inside the Privacy & Security settings.
Also note that the browser checks the server certificate in negotiation and looks at the root authority that signed it. It needs that authority in its store in order to trust the signature. For more information on this, see Microsoft's topic Manage Trusted Root Certificates for managing trusted root certificates for a local computer.
